ON-Device Security
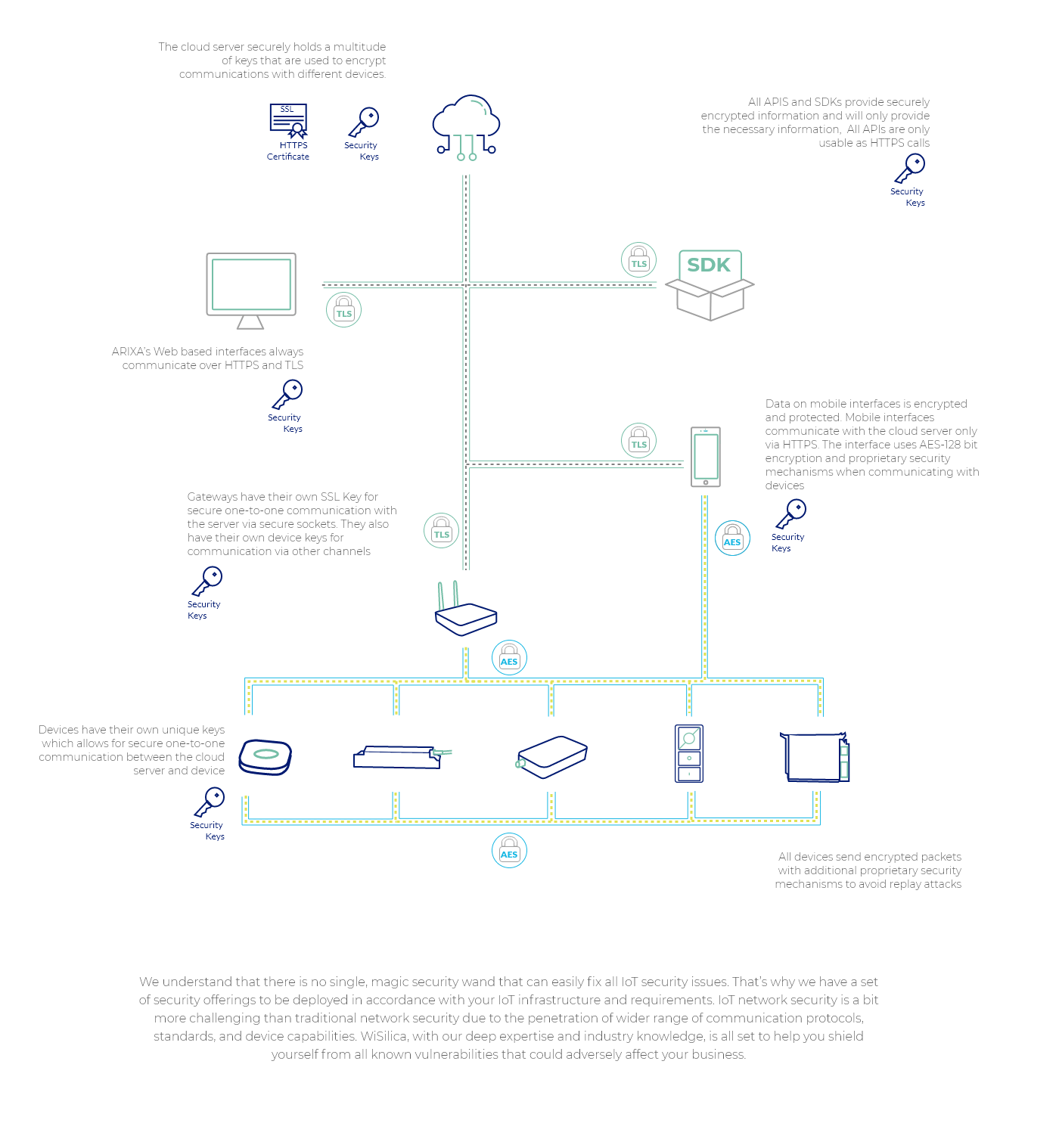
We encrypt every data using standard cryptographic algorithms to ensure data integrity. It is applicable to all your data which is at rest or in transit between IoT edge devices and back-end systems. A Network security Key (NSK) is engaged for message encryption and decryption besides employing an MQTT protocol-based information transfer through secured socket layer. Our 128bit AES encrypted communication prevent message readability, repeatability, and replaceability by unintended parties and stops data sniffing by hackers
WiSilica also employs secured device provisioning with WiSilica cloud API using a unique Device ID and Device Security Key (DSK)

All devices run integrity checks during boot up. Each device has its own individual device key that is burned during manufacture

Communication is encrypted using different keys depending on context

Update files are checksum verified and integrity checked before execution

Cloud Security
To ensure cloud security, we provide complete X.509 digital certifications and cryptographic key including life-cycle capabilities. This is inclusive of public or private key generation, distribution, management, and revocation. Public key infrastructure (PKI), encrypted user credentials, secured API authentication, regular mitigation scanning, and web server and OS hardening are all included and designed to assure you a secured IoT ecosystem. Further, protected infrastructure with TLS based server connectivity, platform monitoring, access controls and OAuth enable added authentication and authorization
WiSilica’s security features also support multi-tenancy with Virtual Private Cloud (VPC) that provide instance and network level isolations
AWS is a highly flexible and secure cloud computing environment, built and managed according to security best practices and standards, with certifications including ISO 27001, SOC 1/2/3 and PCI DSS Level 1
Application Security
WiSilica’s application security system facilitate secured app communication with server using HTTPS and encrypted user sensitive data and device communication. We also ensure that only authorized devices, developers, and apps are involved in communication with APIs in addition to detecting potential threats and attacks pointed towards specific APIs. This approach is effective in safeguarding unauthorized data access to other apps in the bridge to protect your system from data leakage


All devices run integrity checks during boot up. Each device has its own individual device key that is burned during manufacture

Communication is encrypted using different keys depending on context

Update files are checksum verified and integrity checked before execution
SECURITY DURING OPERATION